How to protect yourself against malware
Malware, or malicious software, covers different programs which, when run in devices, cause different types of damage and complications such as interrupting their operations, disrupting how they work, stealing information and displaying unwanted advertising.

The malware industry continues to grow, finding new ways of accessing devices unlawfully both in corporate as well as domestic environment in computers, mobile phones, and increasingly popular Internet of Things (IoT) equipment. That is, a whole range of objects we use daily that are connected to the web. What you have to have clear is that you can never let your guard down with malware.
To protect yourself against malware, you need to know what it is and learn its modus operandi; that is, how it reaches equipment, how it infects it, how it acts and the main consequences of this.
The different variants of malware
Main types and how they act:
1. Virus: by far the most common form of malware consists of an auto-run code that can copy itself and spread from one computer to another with human intervention. One of the most common ways a virus infects devices in webpages is through advertisements which bring you to another compromised page or mail with files or links that are infected.
People help viruses spread by sharing infected files by forwarding mail or messages in instant messaging systems.
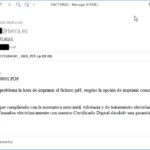
Email with a fake invoice | Source: www.osi.es
2. Worm: this is a variant of a virus that is self-replicating; that is, it reproduces itself in equipment and is designed to propagate itself without human help. An example of this is the automatic sending of it to all the contacts in address books of recipients in email services. The worm replicates itself and in turn is sent to the address book of all recipients and so on in chain-like fashion.
3. Spyware: this type of malware goes through devices looking for keywords, passwords and other valuable information.
4. Trojans: to start off with these appear to be innocuous programs in that the malware is usually “hidden” within a real application; that is, it works by deceit.
They can infect a computer by clicking on an image, a link to a malicious webpage or by opening a file attached to an email. Once the Trojan is inside the device, it can be manipulated for different purposes. Trojans may end up wiping out files or stealing information.
5. Ransomware: the main characteristic of this malware is hijacking. This is a type of malware that prevents or limits access by users to their own system. Most commonly, when the ransomware runs itself, it encrypts files in the hard disk of the victim to force the payment of a ransom in exchange for providing the deciphering key.
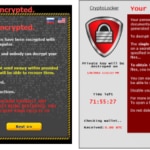
Examples of ransomware | Fuente: www.osi.es
WannaCry is the most recent example of this type of malware.
How do they get into equipment
Most malware arrives in devices through human intervention, either because of a lack of adequate security measures or risky behavior or a combination of both.
Normally, malware is present in infected webpages and devices, fraudulent websites (supplanting the websites of shops and banks), malicious links, attached files included in mass emailing or instant messaging, in file-sharing programs (P2P) and in some types of free software.
Measures to ward off malware
Both in the case of a corporate or personal, fixed or mobile device, you need to count on security solutions, but also, and fundamentally, you have to develop security procedures that allow you to ward off malware.
Malware needs human intervention to get into devices.
- Install an antivirus in all equipment and keep it up to date. It is important to carry out regular security checks using the built-in scanning functions.
- Keep equipment, programs, applications and search engines constantly up to date. These updates include the security patches needed to cover breaches that have been detected.
- Uninstall programs and applications that are no longer used. In the absence of updates, these could be the door that opens for malware.
- Avoid running files or following links that arrive through an email or message that seem strange or comes from unknown sources.
- In the case of mobile devices, only download Google Play o App Store apps, going over ratings and permits beforehand.
- Use tools to detect infected websites. Google provides users with a tool that warns about the risks of a webpage: Safe Browsing.
- Do not connect equipment to USB devices that you do not know where they come from.
- Try to keep up to date on the risks out there. It is advisable to regularly consult the security page of OSI.
- Remember to regularly make security copies in an external unit of the device so as to minimize the loss of information in case of infection.
- It is important to set limits to authorized user sessions in shared equipment to avoid administrator sessions since if a malware gets into a device it will acquire the permits of the session and the fewer the permits there are, the less the damage.
Against malware, being prepared and prudence are as important as the best antivirus in the market.